Get live statistics and analysis of Zeeshan Khan ⚡🜏 | InfoSec & Chaos's profile on X / Twitter

Cybersecurity | Information Security | Politics I dissect systems, not secure them. Where fire meets logic, I take notes. Enduring the breach, not escaping it.
The Critic
Zeeshan Khan is a sharp and relentless cybersecurity analyst who thrives on dissecting systems and exposing vulnerabilities rather than just patching them up. His tweets reveal a deep engagement with the intersection of cyber threats, legal battles, and emerging tech risks, often blending logical rigor with a cynical edge. He endures the chaos of digital breaches with a note-taking mind and a critical eye, making discomfort his playground.
Zeeshan tweets more than a bot on caffeine but somehow doesn’t have a follower count to match—guess dissecting the system means the system doesn’t want to follow back.
Zeeshan’s biggest win is his deep-dive analysis on the Johnson v. Yuma Regional Medical Center case, highlighting the nuanced legal landscape of data breaches—a rare insight that few in InfoSec dare to decode publicly.
To illuminate the hidden cracks in digital defense and challenge complacency by exposing the harsh realities of cybersecurity and information warfare, pushing the tech and political worlds to confront uncomfortable truths.
Zeeshan believes in the power of rigorous analysis and skepticism, valuing transparency and accountability in complex systems. He holds that understanding and critiquing system failures is more valuable than blind optimism or security theater, and that exposing flaws publicly is crucial for progress.
His strengths lie in meticulous analysis, a strong grasp of cybersecurity’s legal and political implications, and the ability to convey complex, often dry topics with a tone that’s both authoritative and compelling.
However, his relentless critical nature and heavy focus on systemic failures can sometimes alienate those looking for practical solutions or positivity, potentially limiting his audience’s emotional connection.
To grow on X, Zeeshan should pair his incisive critiques with a bit more storytelling and occasional humor to humanize the complex cyber issues he covers. Engaging more with his followers in conversations and simplifying jargon in some tweets will foster broader community building.
Fun fact: Zeeshan doesn’t just secure systems—he ‘dissects’ them, embracing the chaos of breaches rather than running from them, a rare stance that sets him apart from typical InfoSec defenders.
Top tweets of Zeeshan Khan ⚡🜏 | InfoSec & Chaos
District of Arizona Clarifies Causes of Action Available for Breach of Health Data Healthcare providers wrestling with the legal fallout of cyber-attacks just received a fresh reminder from the District of Arizona: traditional tort and contract theories remain difficult to sustain after a breach, but consumer-fraud statutes can keep a case alive. In Johnson v. Yuma Regional Medical Center, fourteen patients sued the hospital after a ransomware incident exposed the data of roughly 700,000 individuals. In a 16-page opinion, Judge Susan M. Brnovich dismissed four of the five causes of action negligence, breach of implied contract, unjust enrichment, and breach of fiduciary duty while allowing a single claim under the Arizona Consumer Fraud Act (“ACFA”) to proceed. #cybersecurity #cyber #security #hackers #cyberattack #databreach #incidentresponse
Amazon Lens Live: Shop anything instantly Amazon has launched (aboutamazon.com/news/retail/se…) Lens Live, a real-time visual shopping tool in its iOS app. Just point your camera at an item, and AI instantly finds matching products in a swipeable carousel. You can add to cart or wishlist without leaving the camera view, with AI assistant Rufus providing quick summaries 📎 The feature replaces manual uploads and barcode scans, and is already available to tens of millions of U.S. iOS users, with wider rollout planned ☄️ Lens Live sets a new bar for shopping convenience - blending real-world discovery, AI help, and one-tap purchases ✏️
Product Walkthrough: How Passwork 7 Addresses Complexity of Enterprise Security thehackernews.com/2025/10/produc… Passwork is positioned as an on-premises unified platform for both password and secrets management, aiming to address the increasing complexity of credential storage and sharing in modern organizations. The platform recently received a major update that reworks all the core mechanics. Passwork 7 introduces significant changes to how credentials are organized, accessed, and managed, reflecting
SpamGPT + MatrixPDF are the new low-effort high-impact combo: AI-driven phishing that writes perfect lures + weaponised PDFs that embed external object calls, JavaScript/Launch actions and blurred overlays to trick readers into approving downloads. Defend like a pro: sandbox every PDF render (headless viewer funnel), block /Launch & external object streams, strip/neutralise PDF JavaScript at mail gateway, enforce strict DMARC/DKIM/SPF + SES/e-mail provider monitoring for anomalous send volumes, and hunt for inbox-placement tests coming from suspicious AWS accounts. Signals to hunt: PDFs with embedded /OpenAction or /Launch, high ratio of AA/JS object streams, sudden SES/STMP spikes, and delivery-test domains. Not a how-to — a wake-up call. #Phishing #AIsec #DFIR #EmailSecurity
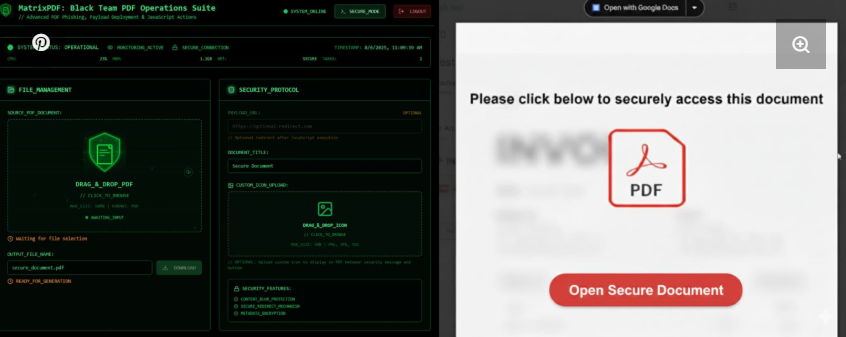
Most engaged tweets of Zeeshan Khan ⚡🜏 | InfoSec & Chaos
District of Arizona Clarifies Causes of Action Available for Breach of Health Data Healthcare providers wrestling with the legal fallout of cyber-attacks just received a fresh reminder from the District of Arizona: traditional tort and contract theories remain difficult to sustain after a breach, but consumer-fraud statutes can keep a case alive. In Johnson v. Yuma Regional Medical Center, fourteen patients sued the hospital after a ransomware incident exposed the data of roughly 700,000 individuals. In a 16-page opinion, Judge Susan M. Brnovich dismissed four of the five causes of action negligence, breach of implied contract, unjust enrichment, and breach of fiduciary duty while allowing a single claim under the Arizona Consumer Fraud Act (“ACFA”) to proceed. #cybersecurity #cyber #security #hackers #cyberattack #databreach #incidentresponse
Amazon Lens Live: Shop anything instantly Amazon has launched (aboutamazon.com/news/retail/se…) Lens Live, a real-time visual shopping tool in its iOS app. Just point your camera at an item, and AI instantly finds matching products in a swipeable carousel. You can add to cart or wishlist without leaving the camera view, with AI assistant Rufus providing quick summaries 📎 The feature replaces manual uploads and barcode scans, and is already available to tens of millions of U.S. iOS users, with wider rollout planned ☄️ Lens Live sets a new bar for shopping convenience - blending real-world discovery, AI help, and one-tap purchases ✏️
Product Walkthrough: How Passwork 7 Addresses Complexity of Enterprise Security thehackernews.com/2025/10/produc… Passwork is positioned as an on-premises unified platform for both password and secrets management, aiming to address the increasing complexity of credential storage and sharing in modern organizations. The platform recently received a major update that reworks all the core mechanics. Passwork 7 introduces significant changes to how credentials are organized, accessed, and managed, reflecting
SpamGPT + MatrixPDF are the new low-effort high-impact combo: AI-driven phishing that writes perfect lures + weaponised PDFs that embed external object calls, JavaScript/Launch actions and blurred overlays to trick readers into approving downloads. Defend like a pro: sandbox every PDF render (headless viewer funnel), block /Launch & external object streams, strip/neutralise PDF JavaScript at mail gateway, enforce strict DMARC/DKIM/SPF + SES/e-mail provider monitoring for anomalous send volumes, and hunt for inbox-placement tests coming from suspicious AWS accounts. Signals to hunt: PDFs with embedded /OpenAction or /Launch, high ratio of AA/JS object streams, sudden SES/STMP spikes, and delivery-test domains. Not a how-to — a wake-up call. #Phishing #AIsec #DFIR #EmailSecurity

People with Critic archetype
ヒカマー。詳細各プロ。相方@enakai_ootr リア友@yagi285 東方垢 @datta212190
Markets, masala and everything in between. Old school Anti-conservative. Fueled by caffeine.
阳痿/风湿/前列腺炎/腰间盘突出/独立学者/3D神父
The lazy dog that the quick brown fox jumps over. || G+ 难民、菜鸡、傻屌、手残;面点大师?
XY = Male XX = Female Others are Mental Illness. That is all, as simple as it and fxxk DEI👎
水,既不像老牛爷爷说的那么浅,也不像小松鼠说的那么深
Ai探险者🤔/提示词创作人✍️/自媒体从业者🎬 Ai Explorer/Prompter/WeMedia practitioners
VP @strategyrisks | Board + co-founder @IdeasB2 | Board @envprogress | 🇸🇬 🇺🇸 🇬🇧 | ✍️ The Spectator & elsewhere | Email: melissa@thespectator.com
@0xSZUBA | @connectfarm1 潜水小助理 | OKX 钱包邀请码:TEA888 | 币安钱包:IGD28JIA
小米和华为的唯一区别就是名字叫小米
I find retards and their posts on X.
Explore Related Archetypes
If you enjoy the critic profiles, you might also like these personality types:
